Privacy at Risk: The Muah AI Security Breach Explained

In recent months, the AI companion app Muah AI has come under scrutiny following a significant hacking incident. This breach not only raised alarms about the app's security protocols but also highlighted broader concerns regarding privacy in the rapidly evolving landscape of AI girlfriend applications.
Causes of the Attack
The hacking incident involving Muah AI can be attributed to several factors:
- Weak Security Protocols: Reports indicate that Muah AI employed inadequate password protections and security measures. Similar to findings from a Mozilla analysis on various romance chatbots, many apps in this space allow users to create weak passwords, making them vulnerable to brute-force attacks.
- Data Collection Practices: Like other AI girlfriend applications, Muah AI collects vast amounts of user data, including personal conversations and preferences. This data is often poorly protected, making it an attractive target for hackers looking to exploit sensitive information.
- Lack of Transparency: Many users are unaware of how their data is stored and used. The vague privacy policies typical of these applications contribute to a lack of user trust and understanding, which can lead to careless data sharing.
Consequences of the Breach
The fallout from the Muah AI hacking incident is multifaceted:
- User Data Exposure: As with many breaches, the most immediate consequence is the potential exposure of personal data. Users may find their private conversations and sensitive information compromised, leading to identity theft or harassment.
- Loss of Trust: Incidents like this can severely undermine user trust in not just Muah AI but in similar applications overall. Users may become hesitant to engage with AI companions due to fears over privacy and security.
- Regulatory Scrutiny: Such breaches often attract the attention of regulatory bodies, which may impose fines or require stricter compliance with data protection laws. This could lead to increased operational costs for companies in the sector.
The Importance of Privacy Security
The Muah AI incident underscores a critical need for enhanced privacy security measures across all AI applications:
- Robust Security Protocols: Companies must implement stronger security practices, including multi-factor authentication and encryption for user data. This is essential not only for protecting user information but also for maintaining company reputation.
- Transparency in Data Handling: Clear communication about what data is collected, how it is used, and how it is protected can help rebuild trust with users. Companies should provide straightforward privacy policies that are easy for users to understand.
- User Education: Users should be educated on best practices for maintaining their privacy online. This includes using strong passwords, being cautious about sharing personal information, and regularly reviewing app permissions.
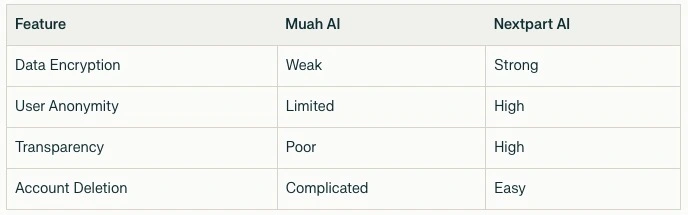
Comparative Analysis with Other AI Girlfriend Applications

While Muah AI grapples with its security issues, other applications like Nextpart AI are taking steps to enhance user safety:
- Nextpart AI employs robust encryption techniques for secure data transmission and storage. It prioritizes user anonymity and offers features that allow users to delete their accounts easily.
In contrast, many competitors still struggle with transparency and security issues. For instance, Romantic AI has been criticized for vague privacy policies and inadequate security measures similar to those that plagued Muah AI.
As the popularity of AI girlfriend applications continues to rise, so too does the importance of prioritizing user privacy and security. The Muah AI hacking incident serves as a cautionary tale for both developers and users alike. By adopting stronger security measures and fostering transparency, companies can not only protect their users but also ensure the sustainable growth of this burgeoning industry.